R01UH0823EJ0100 Rev.1.00 Page 1484 of 1823
Jul 31, 2019
RX23W Group 42. Trusted Secure IP (TSIP-Lite)
42.2.3 Key Installation
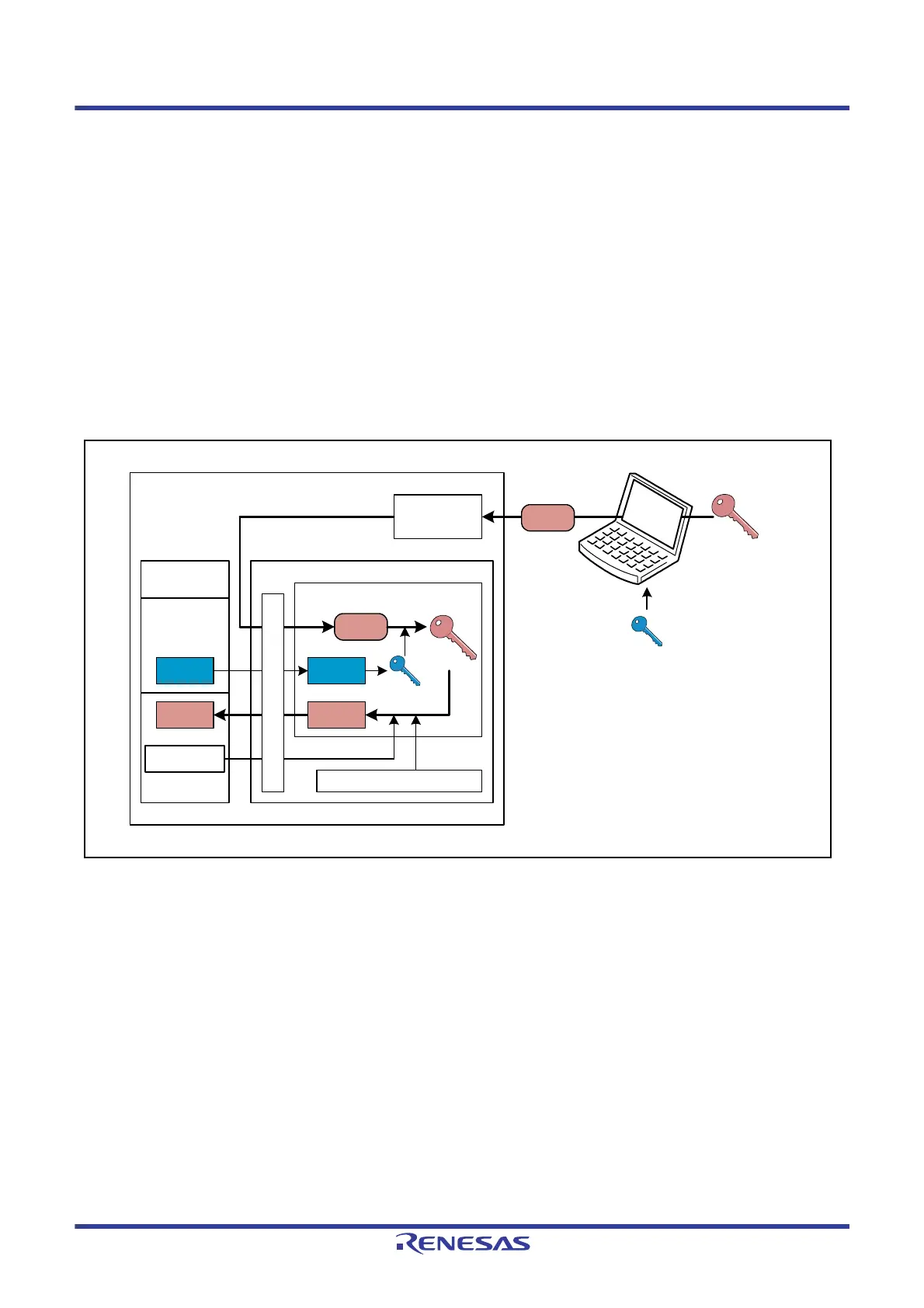
The key installation is the operation that safely converts the user key to the key generation information and stores it in
flash memory. The procedure for installing the key data are given below.
(1) The user uses the key (Key-2) used for encrypting the user key to encrypt the user key (Key-1) producing eKey-1.
(2) The user sends the encrypted user key (eKey-1) to the TSIP-Lite over the serial interface.
(3) The key generation information of the Key-2 (Index-2) contained in the TSIP-Lite library is used to recover the
Key-2, which is then used to decrypt the user key.
(4) The user key is converted to user key generation information (Index-1) using the unique ID and a random number,
and stored in flash memory.
The installation process and flow chart are given in
Figure 42.4 and Figure 42.5, respectively.
Once the key data is installed, the user key generation information (Index-1) can then be used to perform encryption or
decryption.
Figure 42.4 Key Installation Process
MCU
Key-2
Flash
Unique ID
Key-1: User key
Key-2: Key used for encrypting the user key
eKey-1: User key encrypted with Key-2
Index-1: Key-1 key generation information
Index-2: Key-2 key generation information
SCI
eKey-1
Encryption engine
Index-2
eKey-1
Key-1
Index-1
Random number generator
Access management circuit
Key-1
Encrypt
Index-2
Index-1
Key-2
TSIP-Lite
TSIP-Lite
Library

 Loading...
Loading...