The time kept on a device is a critical resource; you should use the security features of NTP to avoid the
accidental or malicious setting of an incorrect time. Two mechanisms are available: an access list-based
restriction scheme and an encrypted authentication mechanism.
Cisco’s implementation of NTP does not support stratum 1 service; it is not possible to connect to a radio or
atomic clock. We recommend that the time service for your network be derived from the public NTP servers
available on the IP Internet.
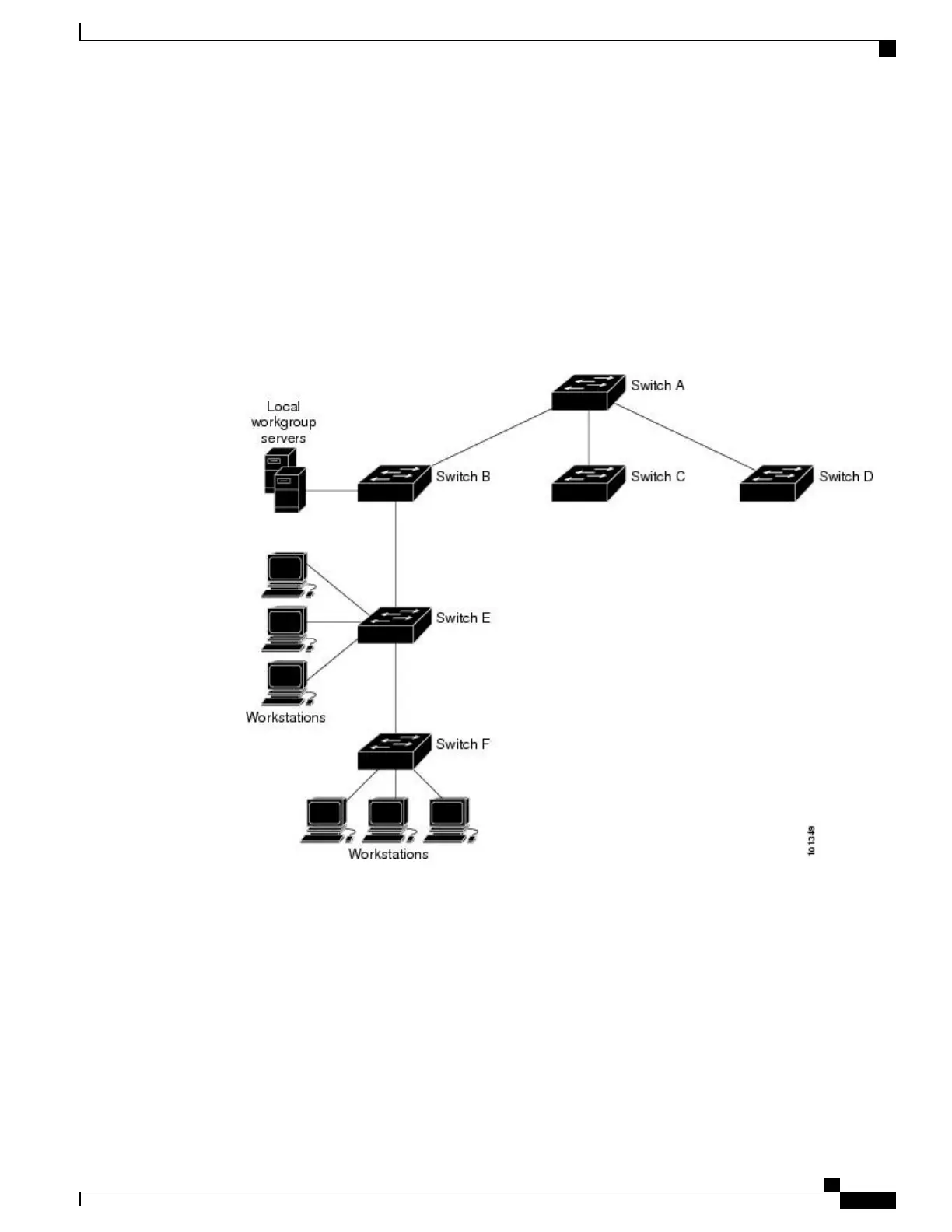
The Figure shows a typical network example using NTP. Switch A is the NTP master, with the Switch B, C,
and D configured in NTP server mode, in server association with Switch A. Switch E is configured as an NTP
peer to the upstream and downstream Switch, Switch B and Switch F, respectively.
Figure 106: Typical NTP Network Configuration
If the network is isolated from the Internet, Cisco’s implementation of NTP allows a device to act as if it is
synchronized through NTP, when in fact it has learned the time by using other means. Other devices then
synchronize to that device through NTP.
When multiple sources of time are available, NTP is always considered to be more authoritative. NTP time
overrides the time set by any other method.
Several manufacturers include NTP software for their host systems, and a publicly available version for
systems running UNIX and its various derivatives is also available. This software allows host systems to be
time-synchronized as well.
Consolidated Platform Configuration Guide, Cisco IOS Release 15.2(4)E (Catalyst 2960-X Switches)
1525
Information About Administering the Switch

 Loading...
Loading...











